If you work in a corporate Unix environment, you probably have a bunch of different Unix servers that you have to login to on a regular basis. And, if you use putty to connect to your servers, you probably end up typing in your password at least couple dozen times a day (double up that number if you are working on a VPN connection that drops couple of times a day like mine!).
So, what is the solution to all of this? Here are a couple of options:
- Use a different Terminal application that provides the ability to store your passwords (like Poderosa, Tectia etc.)
- Use Key-based authentication.
The main problem with #1 is security. When you store your password, it is basically stored in an unprotected fashion on your local hard disk. So, if someone gets to your hard disk someway, they have access to all the servers that you have configured. Also, on a more personal note, I like Putty a lot and have gotten used to it, so I do not want to use a different Terminal.
That leaves us with option #2. Now, there are a lot of great tutorials out there on key-based authentication, so I would not go in detail into that. However, I’ll quickly cover the steps needed to setup key based authentication and the one error that kept me from using it for almost a month!
Prerequisites
We need the following tools installed on your local Windows machine:
- An SSH-compatible Terminal Application (Putty)
- A Key generator (PuttyGen)
- A Key Agent. Optional. (Pageant)
- An SSH-enable Unix/Linux Server
Usually, all the terminals come loaded with all the above mentioned utilities. If not, check the documentation and see if they are compatible with keys generated/stored by some other generator/agent application.
Steps
All the steps shown here will be for Putty’s suite, but you should have similar steps with any other tool:
Generate a Key Pair
A key pair consists of a public and a private key that will be used for authentication with the server. A key pair is like a yin-yang pair. They complete each other! Alone they are useless, but together they provide a very secure method of encrypting data. A piece of information encrypted by a private-key can only be decrypted by the public-key of the same pair and vice versa. Key-based authentication makes use of this fact and splits up the pair between a server and a client machine. The client machine keeps the private-key. To authenticate the client encrypts a pre-agreed message with its private key and sends it to the server. The server tries to decrypt the message using the public-key it has for that client. If the message decrypts properly, the server knows it had to be encrypted with the paired private key and hence you are authenticated.
In a sense, the private key in the key-pair becomes your credentials for the server (and that makes it a really important thing!!!). This is why it is important to protect your private key!
Here are the steps required to generate a key-pair:
- Launch PuttyGen.
- By default, the Parameters section would have ‘SSH-2 RSA’ and ‘1024’ bits options enabled. They should work with most modern system. If your server is using older version of SSH, you can tweak these settings (Check with your Unix admin to know what settings you should use).
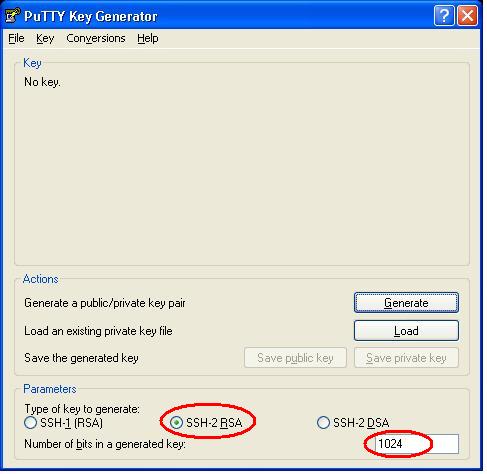
- Click on Generate. A message will come up asking you to move your cursor in the empty space in the window. Do it.
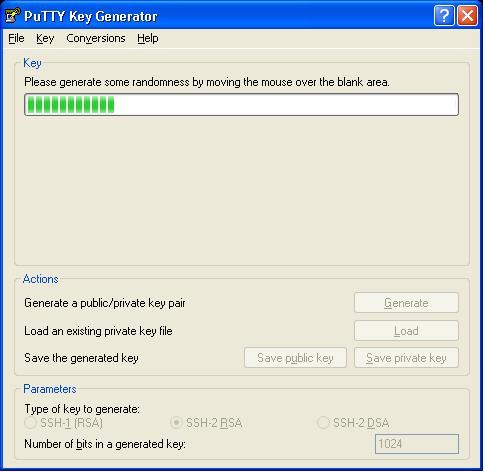
- A key will be generated and displayed.
- Change the ‘Key comment’ field to something which identifies the server(s) you will use this key-pair on, like “Credit-Cards-Accounting” (Yes, you can generate multiple key-pairs for use with different servers). I am not sure if you can use spaces in the comment, but would advise to use some other separator character.
- Enter a passphrase in the ‘Key passphrase’ and ‘Confirm passphrase’ fields. Although, a passphrase is optional, I strongly recommend using it, as it is the only thing that will protect your credentials in case somebody steals them.
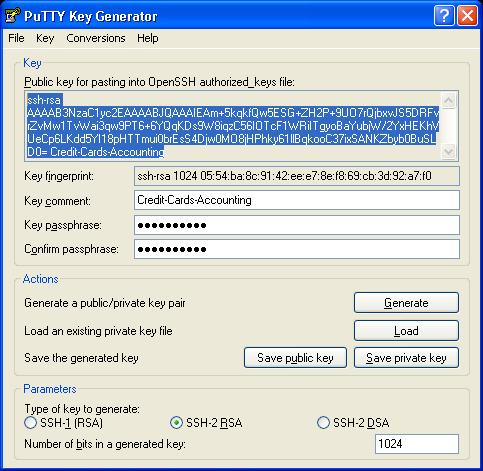
- Click ‘Save private key’ button and save the key in a folder of your choice. I recommend creating a separate folder where you store all your keys and back up that folder whenever you create a new key.
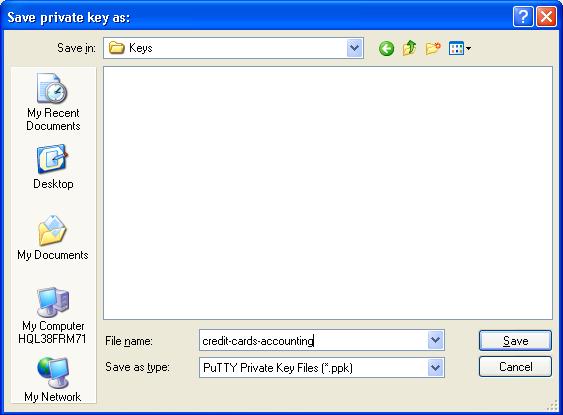
- There is an option to ‘Save public key’, but I much rather prefer copying the public key as displayed on the screen. So select all and copy the public key (Since the private key file contains both public and private keys, you can just load the private key file into Puttygen, if you ever need to copy the public key again).
Setting up the Server
Now that we have the key-pair, the next step is to setup the server to accept the public key of your workstation. My servers use the open-source OpenSSH server, so the following steps are for them. I believe that the proprietary SSH server is not that common and it should also use the same setup (feel free to leave a comment if you use the proprietary SSH sever and you are able to use/not use these steps).
- Login to your Unix/Linux server using the regular password based authentication.
- Create a directory ‘.ssh’ under your home directory. Make sure the permissions are 700 for the .ssh directory.
- cd to the .ssh directory.
- Create a file called authorized_keys and paste the public key in that file. Note that the complete key should be on a single line.
- Change the file permissions on authorized_keys file to 600.
- Make sure that your home directory has the permissions of 755.
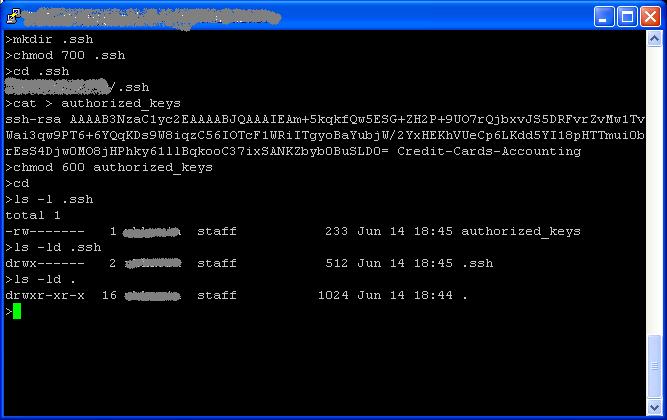
That’s all the setup required on the server end.
Setting up the Terminal Client App
Lets setup a new connection with Putty
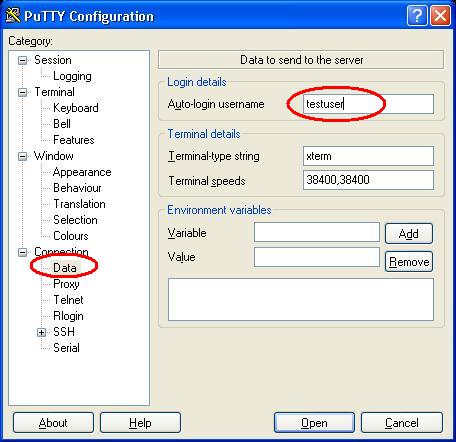
- First we need to setup the connection to use a default user-name. This is not required, but it if you don’t want to enter your password every time, I am assuming you don’t want to type in you user name either. This option is configured under the Connection > Data section, in the ‘Auto-login username’ field.
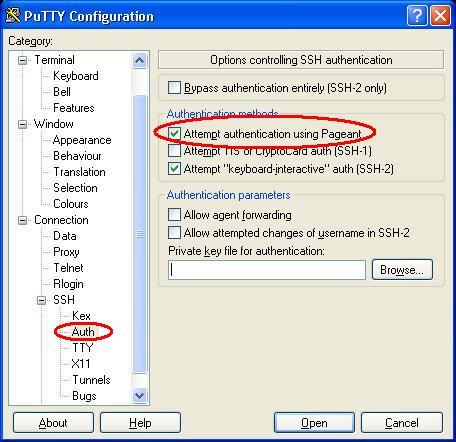
- Next, we need to instruct the terminal to use the private key we just generated. Go to Connection > SSH > Auth section.
- Since we are using an agent to store our private keys, we only need to check the ‘Attempt authentication using Pageant’ under the ‘Authentication Methods’ sub-section.
Setting up the Agent
Since we have our keys encrypted with a passphrase, the only way our Terminal app can access the keys is by asking us for the pass-phrase to decrypt the keys. This defeats the whole purpose, as we have replaced the server’s password with the key’s passphrase. This is where the agent comes in handy. The agent can store your decrypted keys in-memory during your login session on your local machine. This way your keys are always stored encrypted on disk and you do not not have to provide a passphrase every time you use the key. So, the agent strikes a balance between security and usability.
- Launch the agent program (in our case, Pageant).
- Most probably it will start in a minimized mode in the notification area. Double click its icon to show the main window.
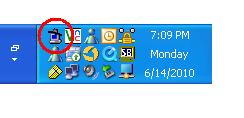
- You would see there are no keys loaded in the agent as yet. Click on the ‘Add Key’ button.
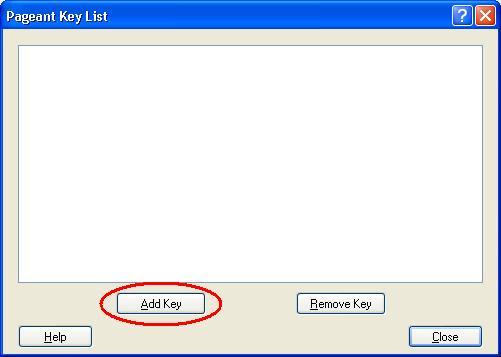
- Browse to the private key file, select it and click ‘Open’.
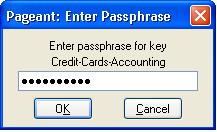
- A dialog box will open up asking for the passphrase for the key. Enter the same passphrase that was used when you created the key-pair using PuttyGen.
- The key would now show-up in the list of loaded keys.
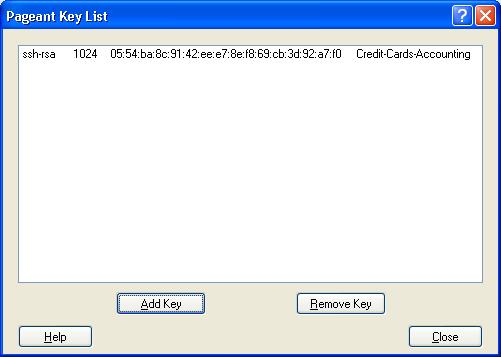
- Repeat last 3 steps for any additional keys you might have.
Note that, you will have to setup the agent everytime you log-off your machine. You can actually create a shortcut to Pageant in the Windows Startup folder with the list of keys to be loaded as command line arguments. This way it will automatically launch and prompt for the key passphrase(s) every time you login.
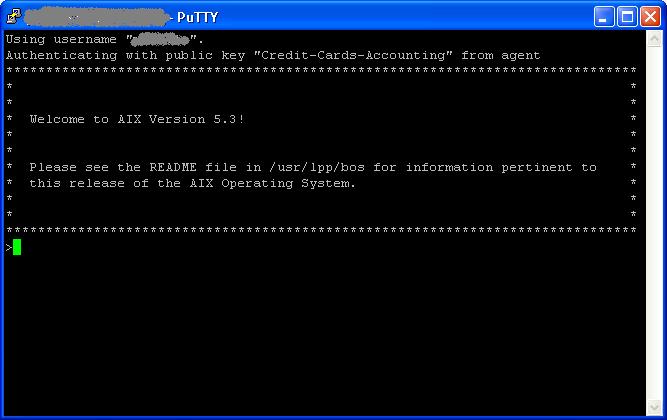
Testing the Setup
Its time to test the complete setup. Launch Putty and select the profile that you have configured to authenticate using the agent. You should see the message that Putty is using the key to authenticate and should be logged in automatically.
Troubleshooting
Server Refused Our Key
The only error that I kept getting was ‘Server refused our key’. If you have run through the setup as mentioned in this article, there could be a couple of reasons why you would get this error:
- You are using OpenSSH and used the wrong format of the public key in the ~/.ssh/authorized_keys file. Remember, copy-paste the public key from the PuttyGen window, not from the ‘public key’ file saved using PuttyGen.
- The permissions on your home directory, the ~/.ssh directory or the ~/.ssh/authorized_keys file are wrong. Double check the permissions as specified in the ‘Setting up the Server‘ section. Note that the home directory permissions are really important… it took me weeks to figure that out! :(
Conclusion
I have been using key based authentication for the last week or so, and I can tell you that I am mighty pleased with the setup. No more frustration of remembering/typing in the password twenty times a day. If you are working in a Unix/Linux environment, I would highly recommend using key-based authentication. There are a lot of other uses of key-based authentication other than interactive login sessions. Perhaps, I’ll cover them in some other post.
Let me know through the comments if this was of help and if I have missed something here!
